Built-In Security
SmythOS is designed with data isolation and zero-trust at its core.
Enterprise-Grade Security, Built In
Secure Agents, From Vault to Execution
Our Security Approach
Like code frameworks, SmythOS gives developers ultimate control over agents while enforcing best practices.
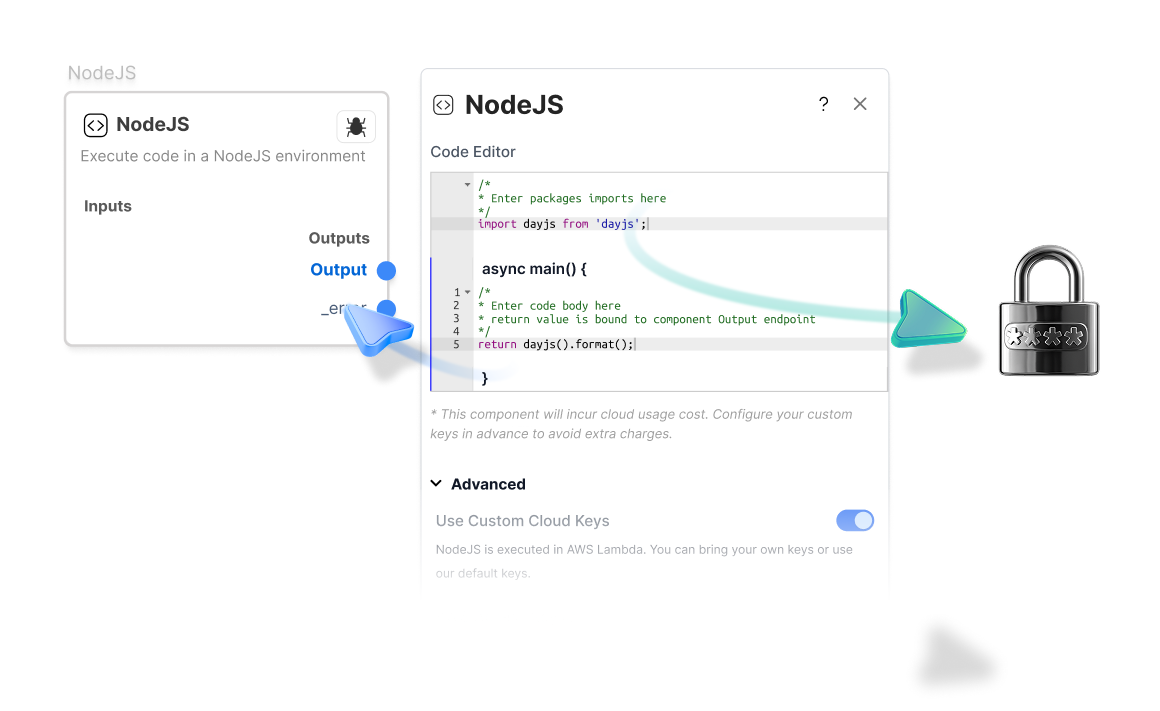
Runtime Advantage
Our runtime is lightweight, modular, and auditable — deployable on edge, cloud, or on-prem.
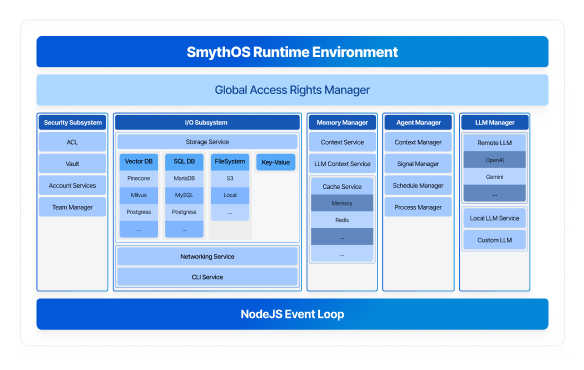
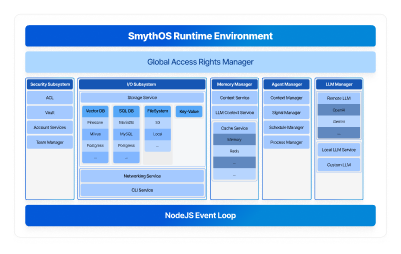
Subsystems & Connectors
Isolation → strict access boundaries Flexibility → local or remote backends Extensibility → easy integration of secure components.
Multi-Agent Security Framework
SmythOS ensures agents can collaborate securely using strict ACL policies and sandbox isolation. Every agent operates independently, with encrypted communication and scoped permissions — preventing data leakage even in complex multi-agent workflows.
Zero-Trust Architecture
Enforcing least privilege and access controls across all components.
Principle of least privilege
Every component and agent operates under the principle of least privilege. There is No implicit trust between components.
Fine-grained ACLs
All interactions are secured with an internal ACL/Candidate system in order to enforce which agents, modules, and users can access specific resources.
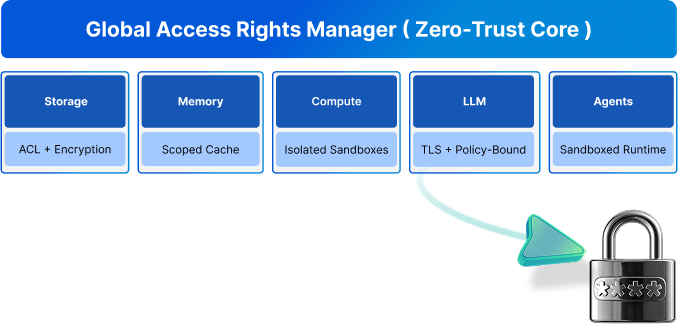
Secure Storage & Data Isolation
Protecting data through flexible backends and strict tenant separation.
Support for On-Premise & On-Device
Deploy SmythOS within your own infrastructure. Data flows stay local, never leaving your environment unless you choose a remote backend.
Flexible Data Storage Options
Choose the backend that fits your needs—local disk/RAM for isolation or secure remote storage like S3 and Redis with enterprise-grade encryption.
Strict Tenant & Agent Isolation
Each tenant and agent runs in a fully isolated context. Connectors are restricted by design, ensuring data never crosses boundaries.
Data Isolation and Encryption at Every Layer
Security isn’t a feature — it’s built into every layer of the SmythOS architecture.
Isolated and Encrypted Systems
SmythOS isolates and encrypts data at every stage — from storage and memory to vector databases and vaults.
Each agent and team operates within its own secure namespace, ensuring that data never crosses boundaries.
All information — files, embeddings, cached memory, and credentials — is encrypted automatically through built-in vault and key management. Developers don’t handle encryption manually; it’s applied transparently by the runtime, keeping innovation fast and security airtight.
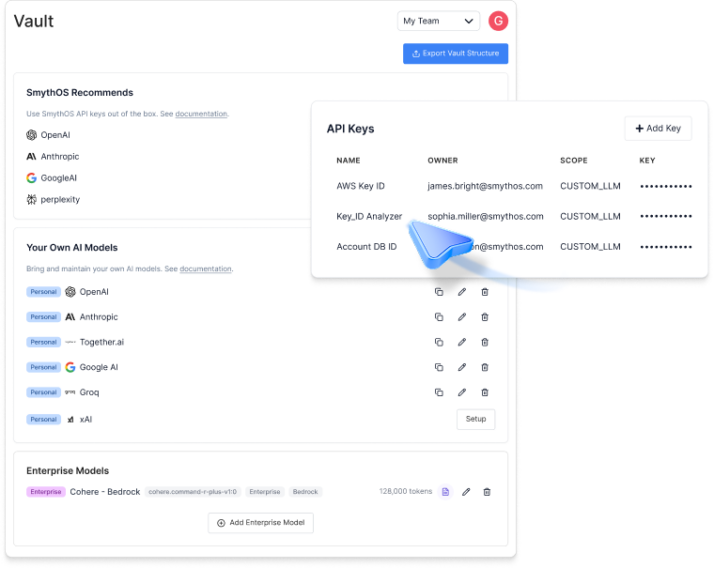
Secrets & Key Management
Vault-based storage and extensible connectors for sensitive data.
No secrets in code
API keys, credentials, and tokens are never hardcoded or stored in application code or agent data.
Policy inheritance
Secrets management is delegated to the configured vault connector, ensuring that the customer’s existing security policies, access controls, and audit trails apply by default.
Extensible design
Custom connectors can be implemented to integrate with other enterprise vault or key management solutions.
Vault-based storage
SmythOS provides secure connectors for managing sensitive data via industry-standard vault systems. Supported integrations include HashiCorp Vault and AWS Secrets Manager.
LLM Security & Deployment Options
Safe integration with public, enterprise, and local LLMs.
Public API Models
Supports LLMs accessible via API (e.g., OpenAI, Google Gemini, Groq, Perplexity). Data sent to these services is transmitted over TLS-encrypted connections, and the handling of that data is governed by the provider’s security and privacy policies.
Hosted Enterprise LLMs
Integrates with cloud-hosted enterprise services such as Google Vertex AI and AWS Bedrock, enabling customers to leverage managed LLM infrastructure while maintaining control over data residency and provider-level compliance.
Local / Self-Hosted Models
SmythOS can run against local LLM deployments (on-premises or in a private cloud). This ensures that all data remains within the customer’s environment, providing maximum control for regulated or sensitive workloads.
Sandboxed Execution
Isolated environments for running custom and untrusted code.
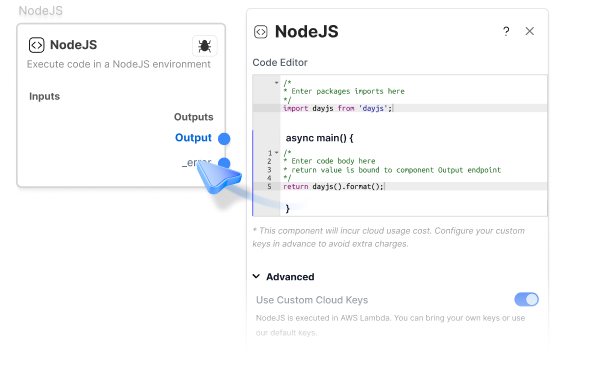
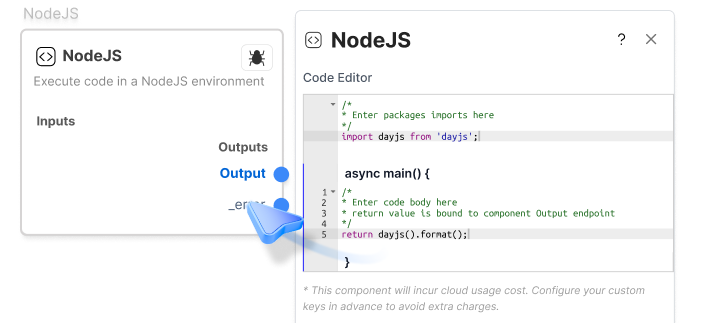
Node.js Execution
Executes inside an AWS Lambda function (or equivalent isolated runtime), providing process-level isolation and resource controls.
JavaScript / ECMAScript Execution
Runs in a fully sandboxed environment with no access to Node.js packages or browser APIs.
Configurable Security
Components can be disabled by or completely removed from the bundles in order to make them unavailable to agents.
Observability & Auditability
Comprehensive logging, monitoring, and redaction for transparency.
Full audit logs
Logs of agent activity, execution flows, and access decisions is available through SRE logging interface, the logs can be set to a high verbose level, or to specifically track some components.
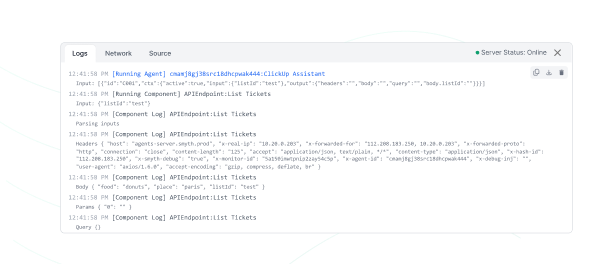
Real-time logging and Monitoring
Provide transparency for debugging, security incident response, and usage tracking of third-party providers, such as LLM tokens, etc.
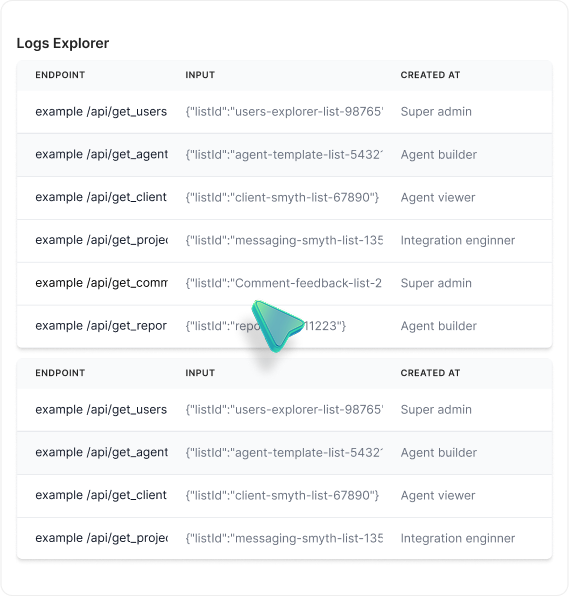
Logs aggregation and redaction
Logs can be aggregated into enterprise SIEM systems for analysis, auditing, alerting.Logs can be partially redacted based on certain patterns and regular expressions.The example below shows an example of automatic redaction of authentication token.
Data Protection & Encryption
Strong encryption for data in transit and at rest across deployments.
In SmythOS SaaS
Data-in-transit is encrypted using TLS 1.2+ to protect communications between clients, agents, and services.
Data-at-rest is encrypted using the cloud provider’s Key Management Service (KMS). Keys are rotated and managed according to provider best practices.
On-Premise Deployments
On-premise deployments can use custom components to leverage host platform capabilities, providing fine-grained control over encryption and key management.
SmythOS already supports custom connectors for third-party Key Management Systems (KMS), including HashiCorp Vault, AWS KMS, and Azure Key Vault.
Deployments can potentially integrate with hardware-based security modules (TPM / HSM) for secure key storage and stronger cryptographic assurance by implementing custom connectors.
Deployment Flexibility for Security Requirements
Protecting data through flexible backends and strict tenant separation.
Cloud (SmythOS SaaS)
Multi-tenant deployment with strict per-tenant isolation. Customer data and agent workloads are logically segregated, ensuring confidentiality and integrity.
On-Premises / VPC
Deployable inside the customer’s own infrastructure (data center or cloud VPC). Guarantees that data never leaves the customer’s environment and enables alignment with internal compliance, residency, and monitoring policies.
On-Device
Lightweight deployment where single or multiple agents are bundled with the Smyth Runtime Environment (SRE) into a standalone executable (.exe). Ideal for highly controlled or offline environments requiring local execution only.
Developers Love SmythOS
Join over 20,000 developers who build with Weaver.