Imagine software that can think for itself, traverse computer networks, and complete tasks on your behalf. This is the reality of mobile agent architectures, a new approach to distributed computing that’s changing how we think about software deployment.
Mobile agent architectures create a framework where intelligent software components can operate independently and migrate across different platforms while carrying their code and data with them. These digital nomads don’t just move; they think, learn, and adapt to new environments, making them incredibly versatile for modern computing needs.
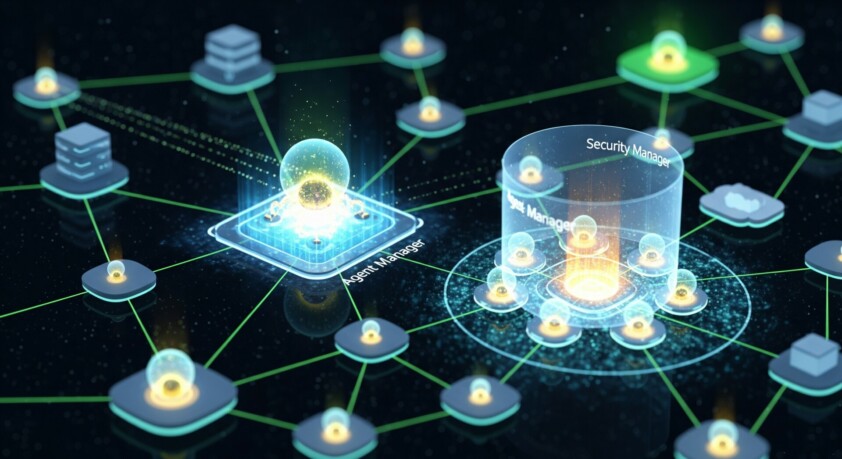
The magic happens through a carefully orchestrated dance of key components. The agent manager acts as both travel agent and welcoming committee, handling the complex logistics of sending and receiving agents across the network. It’s like an airport terminal for software, managing departures, arrivals, and ensuring each agent reaches its destination safely.
Security is paramount in this mobile world, which is why the security manager stands guard like a vigilant bouncer, checking credentials and ensuring only authorized agents gain access to system resources. This watchful guardian protects both the hosting platforms and the agents themselves from potential threats.
Tying everything together is the directory manager, which serves as the yellow pages of the agent world.
Components of Mobile Agent Systems
Mobile agent systems rely on three essential components working in harmony to enable autonomous software entities to move securely across networks. These core elements create a robust and secure distributed computing environment.
The Agent Manager: Orchestrating Agent Movement
At the heart of any mobile agent system lies the agent manager, functioning as the primary controller for agent mobility. This component handles the critical tasks of dispatching agents to remote hosts and receiving incoming agents for local execution. Think of it as an air traffic controller for digital entities, coordinating their movements across the network.
Before an agent embarks on its journey, the agent manager performs serialization—converting the agent and its state into a format suitable for network transmission. This process is similar to packing a traveler’s belongings into a suitcase before a trip. Upon reaching its destination, the agent manager handles deserialization, essentially ‘unpacking’ the agent and reconstructing it in its new environment.
The agent manager also creates the execution context for newly arrived agents, providing them with the resources and environment they need to perform their tasks. This preparation ensures that agents can seamlessly continue their operations regardless of their location in the network.
The Security Manager: Protecting the System
Security stands as a paramount concern in mobile agent systems, making the security manager an indispensable component. According to research on Java-based mobile agents, this component acts as a vigilant guardian, vetting each agent before allowing it to execute.
The security manager performs several critical functions: authenticating agents to verify their identity, controlling access to system resources through defined permissions, and preventing unauthorized activities that could compromise system integrity. It’s akin to a security checkpoint ensuring only authorized personnel can access specific areas of a facility.
In highly secure implementations, the security manager may employ encryption to protect agents during transmission and while stored on disk. It can also authorize agents to pass through firewalls and implement digital signatures to verify agent authenticity.
The Directory Manager: Enabling Service Discovery
The directory manager serves as the system’s information hub, maintaining a comprehensive registry of available agents and their services. This component streamlines service discovery by providing a centralized location where agents can register their capabilities and search for services they need.
Think of the directory manager as a phone book or business directory for agents. When an agent needs to locate a specific service, it consults the directory manager to find the appropriate provider. This component handles both registration of new services and lookup requests from agents seeking particular capabilities.
The directory manager’s role becomes particularly crucial in large-scale distributed systems where hundreds or thousands of agents may offer various services. By maintaining an organized and accessible directory, it significantly reduces the complexity of service discovery and agent interaction.
Security in Mobile Agent Systems
The distributed nature of mobile agent systems introduces unique security challenges that require robust protection mechanisms. These autonomous software entities, capable of moving across networks and executing on different platforms, face threats from both malicious hosts and potentially harmful agents. Implementing comprehensive security measures is essential for organizations deploying mobile agent technology.
One fundamental security mechanism is cryptographic tracing, which creates an authenticatable record of an agent’s activities and movements. As highlighted in research from Springer’s Mobile Agents and Security, this technique allows platforms to verify the integrity of incoming agents and detect any unauthorized modifications to their code or state during transit. When an agent moves between platforms, each host adds a signed entry to the trace, creating an immutable record of the agent’s journey.
Access control policies form another critical layer of security. These policies define and enforce restrictions on what resources and services agents can access within a platform. Platform administrators must balance functionality with security, ensuring agents have sufficient privileges to complete their tasks while preventing potential misuse of system resources. For instance, an agent searching airline booking systems should only have access to public pricing data, not internal system configurations.
Secure execution environments provide containment and isolation for mobile agents, protecting both the host platform and the agent itself. These environments, often implemented through sandboxing or virtual machines, prevent agents from accessing unauthorized system resources or interfering with other agents’ operations. This isolation is particularly important when dealing with agents from unknown or untrusted sources.
The threat landscape for mobile agent systems continues to evolve, with attackers developing increasingly sophisticated methods to compromise agent integrity and platform security. Common attack vectors include code manipulation, state tampering, and denial of service attempts. A malicious host might attempt to extract sensitive information from an agent or modify its behavior to serve malicious purposes. Conversely, a malicious agent could attempt to exploit platform vulnerabilities or consume excessive resources.
Looking ahead, the security of mobile agent systems remains an active area of research. While current security mechanisms provide substantial protection, the dynamic nature of distributed systems and emerging attack vectors necessitate ongoing development of new security approaches. Researchers are exploring advanced techniques like encrypted computing and blockchain-based verification to enhance agent security further. Organizations implementing mobile agent systems must stay informed about these developments and maintain robust security practices to protect their autonomous operations.
Interoperability and Portability of Mobile Agents
Deploying an intelligent software agent that navigates seamlessly between a Linux server, a Windows workstation, and an Android device while maintaining its core functionality and security is a significant challenge in mobile agent systems. Achieving true interoperability and portability across diverse computing environments is crucial.
The Foundation for Intelligent Physical Agents (FIPA) has established standards to enable mobile agents to operate consistently across different platforms. These standards define how agents communicate, migrate, and maintain their functionality regardless of the underlying system architecture. It is akin to creating a universal language and set of rules that all mobile agents can understand and follow.
The Java Virtual Machine (JVM) plays a pivotal role in enabling this cross-platform compatibility. By compiling code into platform-independent bytecode, the JVM creates a consistent runtime environment across different operating systems and hardware configurations. This means a mobile agent written in Java can execute identical operations whether it’s running on a high-powered server or a modest mobile device.
However, achieving true interoperability involves more than just consistent code execution. Mobile agents must handle varying security protocols, resource management systems, and performance capabilities across different platforms. For instance, an agent designed to process large datasets might need to adapt its behavior when moving from a server environment to a resource-constrained mobile device.
The standardization landscape continues to evolve as new challenges emerge. Security remains a particular concern. How do you ensure that an agent maintains its integrity and authentication credentials while moving between systems with different security architectures? Performance optimization across varied hardware configurations presents another ongoing challenge, requiring sophisticated adaptation mechanisms within the agent framework.
The movement towards standardization in mobile agent systems represents one of the most significant developments in distributed computing, enabling truly portable and interoperable software agents.
Foundation for Intelligent Physical Agents Standards Committee
Applications and Use Cases of Mobile Agents
Mobile agents are transforming how distributed systems operate across networks, offering powerful solutions for complex computing challenges. These autonomous software entities can migrate between different network nodes, carrying both code and data to execute tasks wherever they are needed most.
In network management, mobile agents have proven particularly valuable. Rather than continuously sending status updates to a central server, these agents can monitor network equipment locally, dramatically reducing bandwidth consumption. Research has shown their effectiveness in fault detection and network monitoring, where they can autonomously navigate through network nodes to gather performance metrics and diagnose issues.
E-commerce platforms leverage mobile agents to create more responsive and personalized shopping experiences. These agents can traverse multiple databases to compare prices, track inventory, and process orders without constant communication with a central server. When a customer searches for a product, mobile agents can simultaneously query multiple vendors, filtering and aggregating results based on user preferences and real-time availability.
In distributed data processing environments, mobile agents excel at handling large-scale computations efficiently. Instead of transferring massive datasets across networks, these agents travel to where the data resides, perform necessary calculations locally, and return only the processed results. This approach is particularly valuable in scenarios involving big data analytics or scientific computing, where network bandwidth constraints could otherwise become a bottleneck.
The adaptability of mobile agents makes them ideal for resource-constrained environments like sensor networks. In these settings, agents can dynamically adjust their behavior based on available power, memory, and network conditions. They might choose to aggregate data locally when bandwidth is limited or move to nodes with more processing power for complex calculations.
Mobile agents represent a paradigm shift in distributed computing, offering remarkable flexibility in how we process and move data across networks. Their ability to reduce network load while increasing system responsiveness makes them invaluable for modern distributed applications.
Timon C. Du, Associate Professor at The Chinese University of Hong Kong
The deployment of mobile agents in automated software updates showcases their practical utility. Instead of centrally managing updates for thousands of devices, agents can independently assess local system requirements, download necessary components, and verify successful installation. This distributed approach ensures more reliable and efficient software maintenance while minimizing network congestion.
Leveraging SmythOS for Mobile Agent Development
Building autonomous mobile agents has traditionally been a complex endeavor requiring extensive coding expertise and infrastructure management. SmythOS transforms this process with its comprehensive platform that simplifies agent development while maintaining enterprise-grade capabilities.
At the core of SmythOS’s offering is its intuitive visual builder, which changes how developers approach agent creation. Rather than dealing with complex code, developers can design sophisticated agent workflows through a drag-and-drop interface. This visual approach speeds up development cycles and makes agent creation accessible to team members with varying technical backgrounds.
The platform’s built-in monitoring capabilities provide unprecedented visibility into agent operations. Developers can track performance metrics, resource utilization, and agent behavior in real-time. As one developer noted, “SmythOS’s monitoring tools have been invaluable for optimizing our agents’ performance and quickly identifying potential issues before they impact operations.”
SmythOS excels in resource management, handling the complex task of allocating computing power and memory automatically. This intelligent resource orchestration ensures agents operate efficiently without manual intervention, scaling resources up or down based on actual demand. The platform’s automatic resource management frees developers from infrastructure concerns, letting them focus on agent logic and behavior.
It’s like having a Swiss Army knife for building AI solutions tailored to your unique needs. Whether you need a virtual brand ambassador or a process optimizer, SmythOS has you covered.
Security remains paramount in mobile agent deployment, and SmythOS addresses this with comprehensive enterprise-grade controls. The platform implements robust authentication, encryption, and access management features, ensuring agents operate within secure boundaries. This security-first approach makes SmythOS particularly attractive for organizations handling sensitive data or operating in regulated industries.
Integration capabilities set SmythOS apart in the mobile agent development space. The platform offers seamless API connectivity, allowing agents to interact with existing systems and services effortlessly. This interoperability enables organizations to enhance their current workflows with autonomous agents rather than replacing entire systems.
Future Trends and Directions in Mobile Agent Technology
Mobile agent technology is evolving rapidly with advancements in AI capabilities, security, and interoperability. One key development is the integration of homomorphic encryption, which allows computations on encrypted data without decryption, addressing privacy concerns while maintaining robust security.
Fault tolerance mechanisms have also improved, ensuring operational integrity even in challenging conditions, which is crucial for mission-critical scenarios. Integration with IoT devices is another significant trend. As the number of connected devices grows, mobile agents are optimized to interact seamlessly with diverse IoT ecosystems, enhancing automation and data processing at the network edge.
Despite these advancements, the industry must address emerging challenges. As AI capabilities converge with mobile agents, new complexities in system design and security arise. Organizations must stay ahead of these developments to fully leverage mobile agent technology.